Windows update dents 'Autorun' malware prevalence
James Delahunty
22 Jun 2011 10:27
Update earlier this year halts surge of 'Autorun' malware family infections.
Microsoft released an update on February 8 for the Windows XP and Windows Vista platforms. The update targeted the "AutoPlay" feature of the operating system that let an Autorun.Inf file in removal media dictate what to execute immediately upon insertion.
The change would stop the Autorun feature from being enabled automatically on the platforms, except in the case of optical disc media. The update was sent out in response to a surge of detections of malware abusing the Autorun system to spread by removal media (USB sticks etc.)
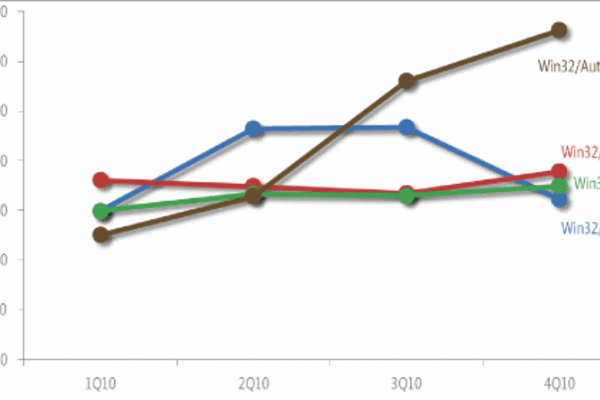
Microsoft security products had tracked the malware under the family Win32/Autorun, and toward the end of 2010, the number of detections on systems skyrocketed past other frequently detected malware such as Win32/Conficker, Win32/Rimecud and Win32/Taterf.
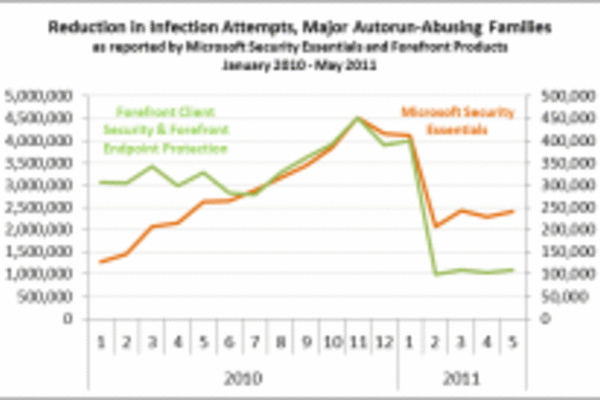
Last week, Microsoft provided some statistics to show how effective the small change to the Autorun feature was at dropping the infection rate (again with data from Microsoft products, such as the Malicious Software Removal Tool delivered via Windows Update each month.)
By May, the number of infections found by Microsoft security products (of the Autorun family) had declined 59 percent on Windows XP systems, and 74 percent on Windows Vista, compared to the infection rates in 2010. The results also varied based on what service packs had been installed, with Windows Vista SP2 seeing an 82 percent decrease.
There was very little difference for Windows XP SP2 since it is out of support and didn't get the update, and likewise Windows 7 wasn't an issue to begin with as it already has a safer Autorun feature built in.
Total infections did not completely disappear because for much of the malware, the Autorun exploitation was only part of their strategy to propagate. On top of that, some of it is downloaded by other malware onto systems.