FBI targets 'scareware' malware peddlers
James Delahunty
24 Jun 2011 0:44
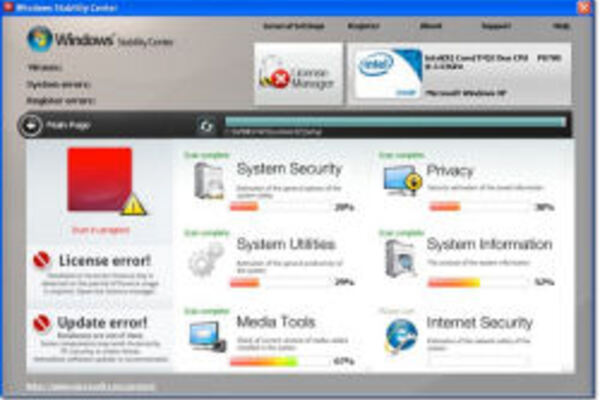
U.S. Feds work with international law enforcement agencies to disrupt two FAKEAV peddlers.
Two Latvian individuals have been indicted, and more than 40 computers, servers and back accounts have been seized as part of Operation Trident Tribunal, which targets peddlers of fake anti-virus scams. It is estimated that the gangs involved caused more than $74 million in total losses to more than one million computer users.
Scareware works by alerting users to fake threats allegedly residing on their computers with terrifying scan results, then offers to clean up the non-existent malware if the user will pay a fee for a full version of the software, using a credit card. There are many ways scareware can show up on a victims' PC, such as being tricked into installing it from a fake alert on a webpage, or it may be downloaded and executed by an existing malware on the computer.
The first of the international criminal groups disrupted by Operation Trident Tribunal infected hundreds of thousands of computers with scareware and sold more than $72 million of the fake antivirus product over a period of three years. An estimated 960,000 users were victimized by the scheme, some paying up to $129. Latvian authorties seized at least five bank accounts that were alleged to have been used to funnel profits to the scam's leadership.
A second scam targeted by law enforcement relied on malicious advertisements (malvertisements) to deliver the scamware. An indictment unsealed in U.S. District Court in Minneapolis charges the two operators of this scareware scheme with two counts of wire fraud, one count of conspiracy to commit wire fraud and computer fraud. The two (Peteris Sahurovs, 22, and Marina Maslobojeva, 23) were arrested by Latvian authorities in Rezekne.
They had created a fake advertising agency and claimed to represent a hotel chain. After convincing the Minneapolis Star Tribune's news website, startribune.com, to carry the advertisements for the fake hotel chains, they changed the advertisements to malicious variants, leading to infection of many readers' computers.
The scam allegedly led to at least $2 million in losses. If convicted, the defendants face penalties of up to 20 years in prison and fines of up to $250,000 on the wire fraud and conspiracy charges, and up to 10 years in prison and fines of up to $250,000 on the computer fraud charge.
"Today's operation targets cybercrime rings that stole millions of dollars from unsuspecting computer users," said Assistant Attorney General Lanny A. Breuer of the Criminal Division.
"These criminal enterprises infected the computers of innocent victims with malicious scareware, and then duped them into purchasing fake anti-virus software. Cyber crime is profitable, and can prey upon American consumers and companies from nearly any corner of the globe. We will continue to be aggressive and innovative in our approach to combating this international threat. At the same time, computer users must be vigilant in educating themselves about cyber security and taking the appropriate steps to prevent dangerous and costly intrusions."