 Researchers over at security firm Symantec have come across a new advanced phishing attack aimed at stealing your Google credentials.
Researchers over at security firm Symantec have come across a new advanced phishing attack aimed at stealing your Google credentials.
The new attack specifically targets Google Docs and Google Drive users. An email will hit your inbox with a subject line of "Documents" or similar, claiming there is an 'important document' stored in Google Docs that you can open by clicking the included link.
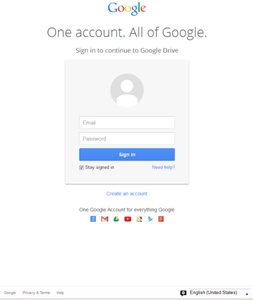
By clicking, you are directed to a Google Docs login page where you are required to input your username and password. The page looks just like the official login page Google uses when you have not signed in for an extended period of time.
The attackers have created a folder on Google Drive to host the phishing page, so the address bar does show Google.com, making the phish very clever for unsuspecting victims.
"The fake page is actually hosted on Google's servers and is served over SSL, making the page even more convincing," Symantec security expert Nick Johnston says. "The scammers have simply created a folder inside a Google Drive account, marked it as public, uploaded a file there, and then used Google Drive's preview feature to get a publicly accessible URL to include in their messages."
"This page then redirects to a real Google Docs document, making the whole attack very convincing. Google accounts are a valuable target for phishers, as they can be used to access many services including Gmail and Google Play, which can be used to purchase Android applications and content," Johnston concluded.
As always, the best way to avoid such a phish is to always login to anything by going to the site or service yourself and not through a link, no matter where it supposedly has come from.
By clicking, you are directed to a Google Docs login page where you are required to input your username and password. The page looks just like the official login page Google uses when you have not signed in for an extended period of time.
The attackers have created a folder on Google Drive to host the phishing page, so the address bar does show Google.com, making the phish very clever for unsuspecting victims.
"The fake page is actually hosted on Google's servers and is served over SSL, making the page even more convincing," Symantec security expert Nick Johnston says. "The scammers have simply created a folder inside a Google Drive account, marked it as public, uploaded a file there, and then used Google Drive's preview feature to get a publicly accessible URL to include in their messages."
"This page then redirects to a real Google Docs document, making the whole attack very convincing. Google accounts are a valuable target for phishers, as they can be used to access many services including Gmail and Google Play, which can be used to purchase Android applications and content," Johnston concluded.
As always, the best way to avoid such a phish is to always login to anything by going to the site or service yourself and not through a link, no matter where it supposedly has come from.













