 A US-led effort has disrupted the operation of the notorious Gameover Zeus botnet and the Cryptolocker ransomware that has cost businesses and consumers millions.
A US-led effort has disrupted the operation of the notorious Gameover Zeus botnet and the Cryptolocker ransomware that has cost businesses and consumers millions.
Gameover Zeus was the latest variant of Trojan.Zbot, designed to steal banking information and other credentials from victims. Instead of using centralized command-and-control servers to control the botnet, Gameover Zues uses a more sophisticated decentralized peer-to-peer system and strong encryption to spread commands around the botnet, and to direct stolen financial information.
(NOTE: The U.S. has also charged as is seeking a Russian man in connection with Gameover Zeus and Cryptolocker)
(HOW-TO: Here are instructions on how to detect and remove Gameover ZeuS from PCs)
The principal purpose of the botnet is to capture banking credentials from infected computers. Those credentials are then used to initiate or re-direct wire transfers to accounts overseas that are controlled by cyber criminals.
According to the FBI, Gameover Zeus has caused more than $100 million in losses. Between 500,000 and 1 million computers are infected, with around a quarter of them thought to be in the United States.
To act against Gameover Zues, the U.S. obtained civil and criminal court orders in federal court in Pittsburgh authorizing measures to redirect the automated requests by victim computers for additional instructions away from the criminal operators. The court order authorizes the FBI to record the IP addresses of infected computers that reach out to the substituted servers under its control, so as that victims can be assisted in removing the malware.
In disrupting the botnet, the FBI was joined by law enforcement agencies all over the world, including the National Crime Agency in the United Kingdom. Private entities also assisted, with the Department of Justice crediting Microsoft Corporation, Abuse.ch, Afilias, F-Secure, Level 3 Communications, McAfee, Neustar, Shadowserver, Anubis Networks and Symantec with assistance.
Attempts to disrupt Cryptolocker
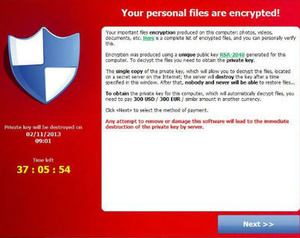
Cryptolocker is a form of ransomware that locks access to a victim's personal files unless a fee is paid. This fee can range up to $700, according to the Department of Justice. In all, Cryptolocker is estimated to have infected more than 234,000 computers, with about half of those being located in the United States. In two months since Cryptolocker emerged in September 2013, it is estimated that over $27 million in ransom was paid.
The difference between Cryptolocker and other forms of ransomware is it uses cryptographic key pairs to encrypt the computer files of its victims. Unless a victim pays the ransom, it is impossible to recover the files at this point.
Due to a coordinated effort between the FBI and several of its overseas counterparts, and multiple private sector entities, the computer servers acting as command and control hubs for the Cryptolocker malware have been seized.
How do computers become infected?
Gameover Zeus spreads primarily by e-mail messages that trick users into running malicious attachments. Once the attachment is run, the Gameover Zeus malware is downloaded and the machine is infected. After this point it will sit quietly and wait for the victim to carry out online banking or other financial transactions, interrupting the process to steal important information that can be used to carry out fraud later.
For example, the malware can grab login information and attempt to login itself in order to carry out money transfers or other fraudulent acts. If the remote bank finds the request or login suspicious, it can prompt the malicious source with additional security questions. At this point, the malicious source can relay the request for additional security information to the victim. Once answered, the information is passed to the malicious source, which then relays it to the remote bank/financial institution, and now it can do as it pleases.
The Cryptolocker malware is strongly linked to the Gameover Zeus botnet, which is its primary means of delivery to a victim's PC, and both are linked to the same group.
CONTINUE READING: U.S. identifies Russian linked to Cryptolocker, Gameover Zeus
(NOTE: The U.S. has also charged as is seeking a Russian man in connection with Gameover Zeus and Cryptolocker)
(HOW-TO: Here are instructions on how to detect and remove Gameover ZeuS from PCs)
The principal purpose of the botnet is to capture banking credentials from infected computers. Those credentials are then used to initiate or re-direct wire transfers to accounts overseas that are controlled by cyber criminals.
According to the FBI, Gameover Zeus has caused more than $100 million in losses. Between 500,000 and 1 million computers are infected, with around a quarter of them thought to be in the United States.
To act against Gameover Zues, the U.S. obtained civil and criminal court orders in federal court in Pittsburgh authorizing measures to redirect the automated requests by victim computers for additional instructions away from the criminal operators. The court order authorizes the FBI to record the IP addresses of infected computers that reach out to the substituted servers under its control, so as that victims can be assisted in removing the malware.
In disrupting the botnet, the FBI was joined by law enforcement agencies all over the world, including the National Crime Agency in the United Kingdom. Private entities also assisted, with the Department of Justice crediting Microsoft Corporation, Abuse.ch, Afilias, F-Secure, Level 3 Communications, McAfee, Neustar, Shadowserver, Anubis Networks and Symantec with assistance.
Attempts to disrupt Cryptolocker
Cryptolocker is a form of ransomware that locks access to a victim's personal files unless a fee is paid. This fee can range up to $700, according to the Department of Justice. In all, Cryptolocker is estimated to have infected more than 234,000 computers, with about half of those being located in the United States. In two months since Cryptolocker emerged in September 2013, it is estimated that over $27 million in ransom was paid.
The difference between Cryptolocker and other forms of ransomware is it uses cryptographic key pairs to encrypt the computer files of its victims. Unless a victim pays the ransom, it is impossible to recover the files at this point.
Due to a coordinated effort between the FBI and several of its overseas counterparts, and multiple private sector entities, the computer servers acting as command and control hubs for the Cryptolocker malware have been seized.
How do computers become infected?
Gameover Zeus spreads primarily by e-mail messages that trick users into running malicious attachments. Once the attachment is run, the Gameover Zeus malware is downloaded and the machine is infected. After this point it will sit quietly and wait for the victim to carry out online banking or other financial transactions, interrupting the process to steal important information that can be used to carry out fraud later.
For example, the malware can grab login information and attempt to login itself in order to carry out money transfers or other fraudulent acts. If the remote bank finds the request or login suspicious, it can prompt the malicious source with additional security questions. At this point, the malicious source can relay the request for additional security information to the victim. Once answered, the information is passed to the malicious source, which then relays it to the remote bank/financial institution, and now it can do as it pleases.
The Cryptolocker malware is strongly linked to the Gameover Zeus botnet, which is its primary means of delivery to a victim's PC, and both are linked to the same group.
CONTINUE READING: U.S. identifies Russian linked to Cryptolocker, Gameover Zeus














