 Google's Chrome is considered to be among the safest browsers for a good reason. Google has spent copious amount of time providing users with the most secure browser they can make, and largely they've succeeded.
Google's Chrome is considered to be among the safest browsers for a good reason. Google has spent copious amount of time providing users with the most secure browser they can make, and largely they've succeeded.
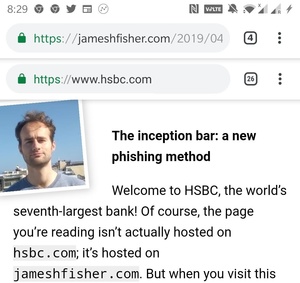
However, there are always going to be problems that haven't been taken care of and exploits that could happen at any given time. One of these is, what a software developer Jim Fisher calls the inception bar.
He has figured out a way to fool users with a fake address bar on Chrome for Android. People can usually rely on their address bar showing valid information, but with this exploit Fisher has managed to replace it fairly convincingly with a fake URL bar.
When you scroll down on Chrome for Android, the address bar slowly slides away, normally when you go back up it's waiting for you again at the top. With the exploit Fisher's bar appears at the top and won't be replaced with the actual one even when scrolled up.
There are, fortunately, a few ways to determine that you are indeed seeing a fake bar and not a real one. First, at least with this iteration of the code, it appears in the middle of scrolling down, which should raise some concerns.
If you aren't sure if this is indeed a fake bar still, you can lock and unlock the device to reveal the actual bar, after which the fake bar is shown below (pictured above).
If you'd like to try and see how real the bar indeed looks in action, head to James Fisher's blog on an Android device and give it a try. If you don't have an Android device handy, he has a video demonstrating the effect.
Needless to say that if you come across one of these exploits in the real world, you probably shouldn't be trusting the website.
He has figured out a way to fool users with a fake address bar on Chrome for Android. People can usually rely on their address bar showing valid information, but with this exploit Fisher has managed to replace it fairly convincingly with a fake URL bar.
When you scroll down on Chrome for Android, the address bar slowly slides away, normally when you go back up it's waiting for you again at the top. With the exploit Fisher's bar appears at the top and won't be replaced with the actual one even when scrolled up.
There are, fortunately, a few ways to determine that you are indeed seeing a fake bar and not a real one. First, at least with this iteration of the code, it appears in the middle of scrolling down, which should raise some concerns.
If you aren't sure if this is indeed a fake bar still, you can lock and unlock the device to reveal the actual bar, after which the fake bar is shown below (pictured above).
If you'd like to try and see how real the bar indeed looks in action, head to James Fisher's blog on an Android device and give it a try. If you don't have an Android device handy, he has a video demonstrating the effect.
Needless to say that if you come across one of these exploits in the real world, you probably shouldn't be trusting the website.













