security

Sometimes it can be tempting to avoid updating to a new Android version. What happens if you decide to delay major updates to the OS?
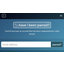
Massive database of leaked passwords and login details published. You can use it to check if your account has been hacked.

As the details of the CCleaner malware fiasco unfold, it has become clear that the hack wasn't just sophisticated, but a targeted espionage attempt.

CCleaner distributed malware with its official download for several weeks before it was noticed by security experts. Company who found the malware calls the hack that made it possible a very sophisticated one.

We built a tool to check if your Spotify account has been leaked, along with its password details, to public. Today, a list of more than 6'000 ......

During the past 24 hours, there has been a massive wave of phishing attempts targeting Facebook page owners, such as entrepreneurs and hobby groups.
......

According to Valve, 77,000 Steam accounts are hijacked every month, and the company is trying to fight back.

Amazon has finally moved ahead in securing your account, adding two-factor authentication.

Microsoft has selected an end-of-life date for older Internet Explorer browser versions, giving users until January 12, 2016 to use all versions before IE 11, if they want to keep up-to-date security that is.

According to Cisco's security research, Microsoft's Silverlight is now the most vulnerable and dangerous plugin, surpassing perennial list toppers like Java and Flash.
Twitter has finally added new security features including the ability to reset their passwords via SMS, and the addition of suspicious logins notifications.

About a month ago Adobe confirmed that their systems were breached and user account details were compromised. Security researchers and hackers ......

5 steps you can take to decrease the security risks associated with using a Microsoft account in Windows 8

On Friday, Apple made headlines by purchasing the publicly traded biometrics company AuthenTec for $356 million.
In doing so, it appears ......
Insecure third-party applications in Windows provide an attractive attack vector, even against systems that have all Windows security updates installed.

A security researcher appears to have verified Carrier IQ's claim that their smartphone software does not log keystrokes or SMS messages.

Thanks to its second high-profile case in which an employee lost a prototype of an upcoming iPhone, Apple is hiring two new security personnel ......

A new report highlights several security deficiencies in modern automototive electronics systems.
The report was released by McAfee in partnership ......

According to Internet security expert John Bumgarner, Sony's computer networks are still not fully secured, even 28 days after hackers attacked ......

BusinessWeek has posted a nice concise report on how secure most passwords are, and how long it takes even hackers to guess it.
As it has ......
| Older entries |








